John Podesta’s Email Hack Should be a Lesson for All
The hack of the DNC and Hillary Clinton’s Campaign Chairman, John Podesta, may fade away as the news media turns its attention to the transition of power and next big story, but an important issue for business executives and board members is not the politics of the hack, but how it happened. It could easily happen to anyone, causing damage and harm to you, your reputation, your company and your colleagues.
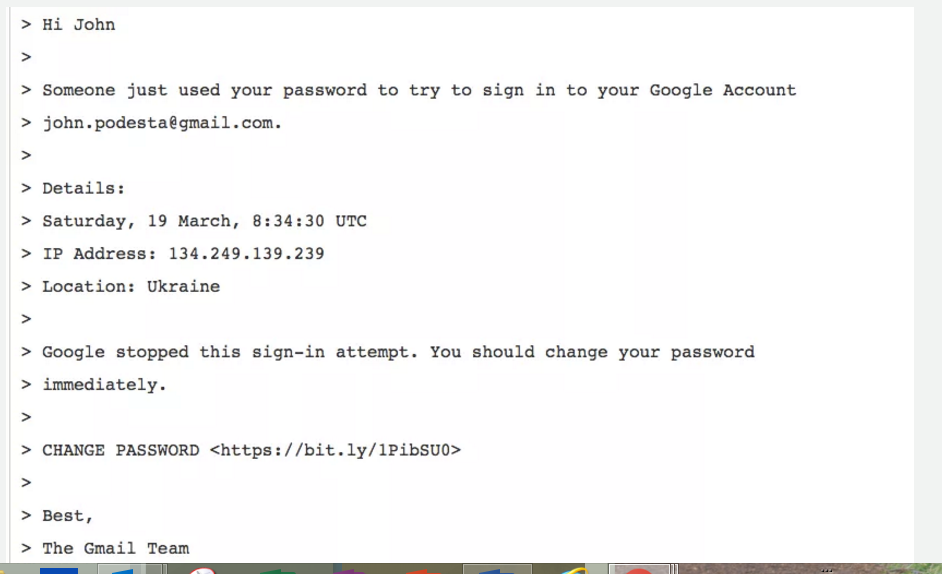
So, let’s take a moment to dissect exactly what happened. Podesta received a phishing email from no-reply@accounts.googlemail.com that appeared to be from Google requesting him to change his password. Notice in this email the bit.ly link – this is the key.
He forwarded it to his IT team to confirm that he should reset his password. His IT team then informed him that he should reset the password and provided a clean link to use to reset the password and recommended a two-factor authentication (meaning you get a code on your phone or multiple sources to reset your password – thus more secure). Unfortunately, Podesta somehow went back to the phishing email and clicked on the link, thereby allowing the hackers to have access to his gmail account. Unknowingly, he let the bad guys in. It’s like leaving your door open and going on vacation and then being surprised you got robbed.
Most security breaches are a result of someone mistakenly allowing the hackers access. So what does this mean, what is the lesson to learn?
There’s really two issues here:
- How do you prevent these types of hacks?
- Should we continue to use email for so many sensitive or conversational matters?
So, let’s start with the first issue. Hacks can never be fully prevented. I interview and talk with cyber security professionals regularly and the common belief is that as soon as you develop tools to stop the bad guys, they create new tools. It will never be a fully solvable problem, but there are ways to mitigate the attacks. For senior executives and board members a first key step is to ensure that your CIO is fully supported, given resources and funding to implement plans, technology and tools to identify, stop and mitigate bad and malicious activity directed at your company. I write at length about this in Chapter Two of my new book, Digital in the Boardroom. There should be an annual independent cyber threat audit and the board should have a clear and objective picture of the threats facing the. This “independent audit” has been place in accounting for years, why should the threat not be treated with the same level of importance?
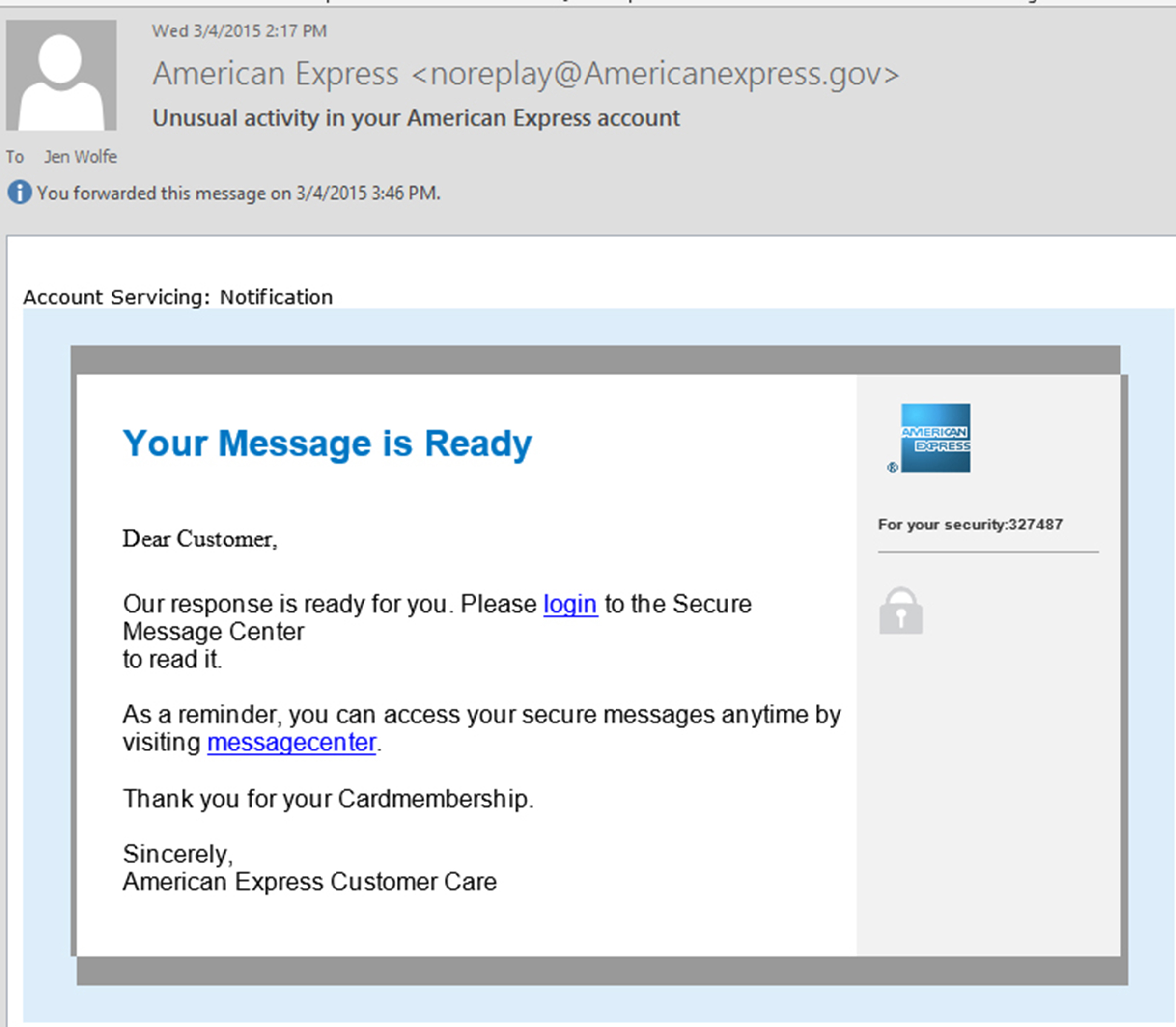
Additionally, senior executives and board members need to exercise extreme caution when clicking on a link to ensure it is from a trusted source. Phishing sites are designed to confuse even savvy and sophisticated executives. So when it comes to clicking on a link, particularly one to reset a password, be extra cautious. I write regularly about the new top level domains. This is one way companies could minimize the “typosite” that looks confusing. American Express is often duped by a company using an americanexpress.gov, which is not them. See the image below – this is a phishing email. They could put a dent in this by using their top level domain, Dot AmEx for all communication with their customers.
Now, let’s address the other issue. With the release of thousands of embarrassing emails to President Obama, Hillary Clinton and her staff alongside the not too distant memory of embarrassing emails released about Sony executives and celebrities, will email conversations hush to a quiet?
While it’s not likely email will die, or go away entirely, senior executives will likely stop using email as a means of conversation and dialogue. I anticipate we will see a return to actual phone calls and face-to-face meetings for important discussions and relationship building.
As cyber security experts know all too well, there is only so much that can be done to prevent a cyber attack. There are certainly best practices and mitigation plans and technology that can help to minimize this exposure, but if someone wants into your system badly enough, they will likely find a way to do it (or the right person to prey upon).
This realization will change the way many continue to use electronic communication. While in ligation lawyers often go to painstaking efforts to protect privileged communication from discovery or presentation in a lawsuit, the reality is if someone just wants to embarrass you, nothing will stop them from releasing it to the court of public opinion, who quite frankly doesn’t care if you think it was subject to some sort of legal privilege. It will be out there and the damage to your reputation, your company, and career will be done, forever.
So many of us have become accustomed to the idea that an email or text is a one-to-one communication, unlike social media which is one to many. We believe that these conversations are private. But if you’ve ever accidently replied to all or sent an email to the wrong person when autofill pulls up the wrong email, you’ve felt the horror of someone seeing something they shouldn’t have seen. Now imagine that same communication out to the entire world. Savvy executives will simply stop using email for actual conversations, dialogue, opinions or anything other than benign schedule setting or simple messages that you wouldn’t care if the whole world knew you sent.
We may see a return to the custom of picking up the phone and speaking to someone or scheduling a face-to-face lunch where the real conversation can occur without the risk of that conversation being read by millions possibly months or years later. And, is that such a bad thing? It takes a little more work to make a phone call, but don’t you get so much more out of it? And, face to face meetings might require a little more effort and sometimes travel, but doesn’t it make for a richer and more meaningful discussion and relationship? These are things we have sacrificed for speed and convenience.
Interestingly, the millennial generation may not feel the impact like those of us in Gen X, Gen Y or Baby Boomers. Millennials never built the habit of using email for conversations, however their use of social media could eventually suffer the same fate as they begin to realize the negative impact their one-to-many conversations have as their lives and careers progress. What is acceptable at 22 is not so much at 32 or 42, but with social media, it’s all just out there to be found and used against you when someone needs to find a reason. Think of how these emails have been used against senior executives and politicians in just the last few years. Social media history will ultimately be the same, only rather than because of a hack, these are messages users have intentionally and willingly posted to the masses. There’s a lot to unpack here between emails and use of social media. C-Suite Execs and Board members should heed the warning and carefully consider how email is used and best practices to protect yourself and your company.